Tax season brings to mind two famous Donald Rumsfeld quotes — The first maligning IRS for an overly-complicated tax return process, but the second, and more relevant, about the fear of the “unknown unknowns” — things we do not know that we do not know.
If you were to ask a dozen SOC leaders “What does threat hunting mean to you?” you may get a dozen answers, but to us, a solid tenant of being able to detect “unknown unknowns” is being able to quickly detect and triage outliers across your detection stack. To some folks, imaging a world where they can detect a true needle in the haystack feels insurmountable, so throughout a series of blogs, we’ll propose concrete hunting techniques that will work to surface those interesting needles.
Below, we’ll highlight three pivots that we have used to uncover thousands of targeted threats inside hundreds of enterprise networks. This is not an exhaustive approach, does not require expensive whiz-bang tech, and will be not the last blog on this topic. This series of blogs is intended to demystify threat detection, and what will work equally well against red teams, targeted crimeware, or APT actors.
- Enterprises should be able to put eyeballs on each and every alert that contains a password protected object every single day. It’s highly unlikely you receive more than three alerts per day, and in the event one day you receive hundreds, they are likely all from the same scattershot spam-type campaign, and can be easily bucketed. The first step, of course, is being able to programmatically detect if your trusty vendor has found one of these threats.
- The world is a big place, and while you may be unlucky enough to be Aaron Aagaard working at AAA, you probably aren’t. If you are still one of the only people to see even a single fragment of a threat 24 hours later, it deserves an eyeball. Think initial dropped hash, delivery URL, c2 domain, etc.
- There is a small number of legitimate email deliverability monitoring tools. If an email contains a hidden mechanism to figure out if you opened the mail, that may deserve an eyeball, when combined with other indicators.
That being said, let’s highlight some examples of these techniques used in the wild to turn over interesting threats. These were found on VT but we run similar detections on our customer data.
Password-protected content
Enterprise tools rarely generate alerts for content that is password protected — think office docs, zip files, or rar archives. Take for example this password protected zip file targeting Israel, containing usage of Atera, legitimate IT management software. Although the password “123456” may not be complex, it shows an attacker with more than zero forethought crafted the email — this category of alert will show up no more than a couple times a day. There’s no substitute to a human eyeball giving a quick glance at a lure to improve the gut-tribution score. If an IT user is running an RDP-type tool, you’ll likely contextualize it, but in contrast, if a sales person is downloading VNC, you may have an issue
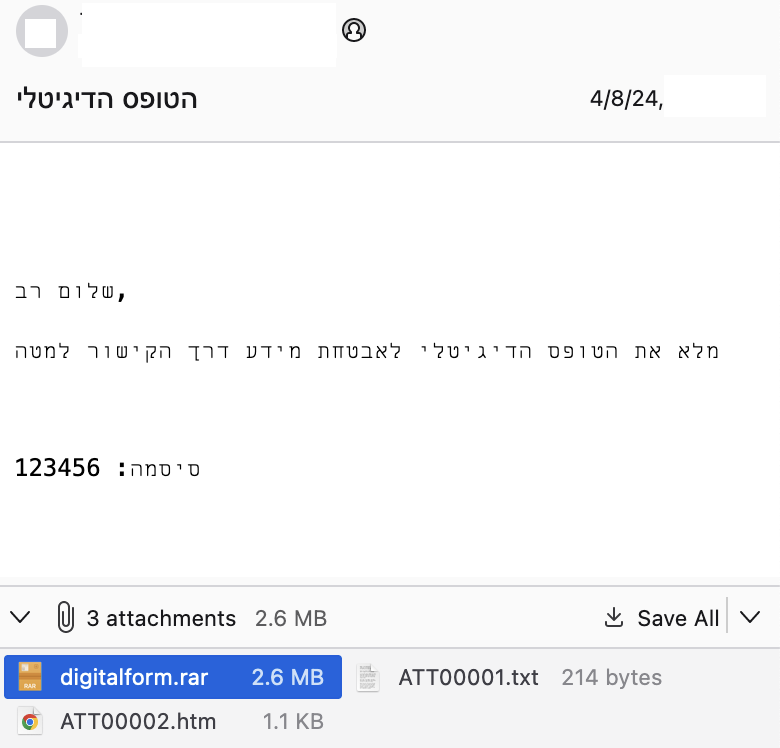
Figure 1: Israeli targets from a compromised IL sender
| hash | filename | notes |
|---|---|---|
| 8a2d14f60c0e69412856aa697706b9cbb8ceed524e4321c25332dad4618dff1e | digitalform.rar | pass protected ‘123456’ |
| 09e09503962a2a8022859e72b86ad8c69dcbf79839b71897c0bf8a4c4b9f4dd6 | digitalform.msi | Atera dropper |
| a96a0ba7998a6956c8073b6eff9306398cc03fb9866e4cabf0810a69bb2a43b2 | AteraAgent.exe | “C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe” /i /IntegratorLogin=“ouamar.mounia[@]airalgerie.dz” /CompanyId=“1” /IntegratorLoginUI="" /CompanyIdUI="" /FolderId="" /AccountId=“001Q3000009snPyIAI” /AgentId=“52e0fc3d-3662-47c2-a6da-c687c013c2d0” |
Figure 2: payloads from Israeli phish
Frequency analysis to find outliers
When looking at true outliers, we want to very quickly be able to determine
- is this a false positive, as most outliers will be (your vendors may appreciate the QA!)
- is this a polymorphic threat that is defeating my “uniqueness” filters
- is this potentially targeted
Analyzing this email thread, one can tell right away that it is not a FP. The sender domain is clearly compromised to send the phish. Looking one layer deeper to understand whether it is polymorphic, you should first extract all URLs programmatically, and have a number of searches already executed. These enrichments should be cheap both computationally and time-wise.
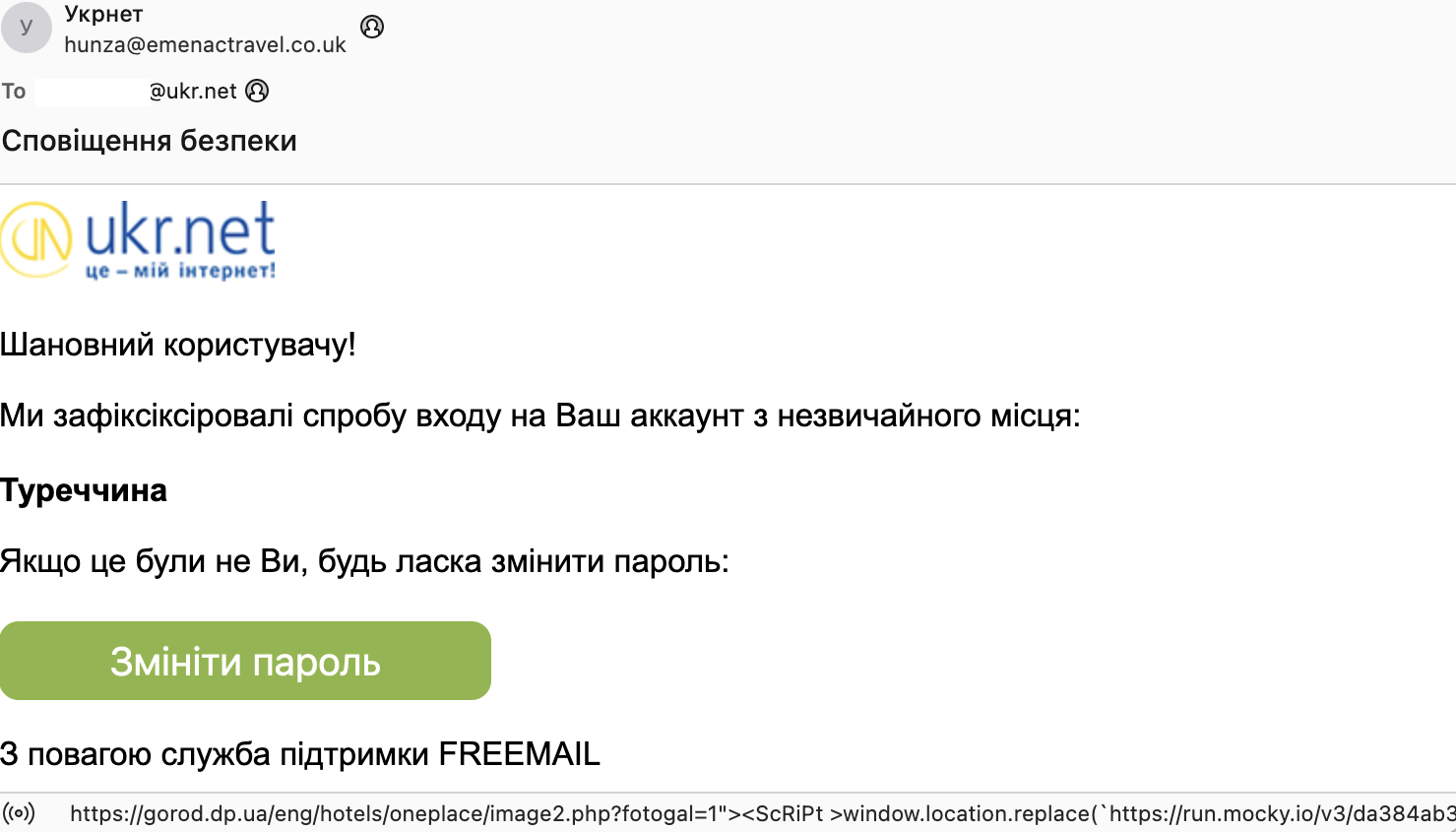
Figure 3: An attacker leveraging a compromised site for hosting XSS->JS
| URL | Why interesting? |
|---|---|
| http://kjghfkfgfdytku.infinityfreeapp[.]com/?usr=[removed]@ukr.net | Anytime there are zero google results for the base domain you should take note |
| https://gorod.dp[.]ua/eng/hotels/oneplace/image2.php?fotogal=1%22 | Your eyes may notice an obvious XSS, but also consider that it is largely unnecessary. If you can get a victim to click on a link, and you aren’t trying to execute JS in a particular domain context, the only real reason is to leverage the reputation of the exploited domain. In this case, a Ukrainian hotel. |
| https://run.mocky[.]io/v3/da384ab3-f749-42d5-a076-40c248dece9b | If this were broadly distributed, you can expect dozens of scans/uploads on VT or Search - urlscan.io |
Figure 4: Initial artifacts can be automatically extracted and enriched with public sources for frequency
The first url leverages a hidden image to track whether the email is opened, and by what type of client. This shady technique is rare but sadly not unheard of for mass mailers. Similarly, Meta recently noted noted an unrelated espionage actor that leveraged canary images inside word documents, to track where and if a benign document was opened. This tried and true technique is a worthwhile attribute to note, even if it requires a bit of manual tuning.
Examining a subset of other mocky-hosted JS, we can see related content, leveraging fingerprinting techniques from output from ipapi.co, used to detect details about the client. Although we shy away from leveraging other vendor names without confirmation, IBM recently put out a report that covers similar delivery from slices of this group, as did Proofpoint, Trend Micro, and TAG.
| hash | mocky | analysis notes for readers to pivot further on VirusTotal |
|---|---|---|
| a3c697da262af1d606faeb5896c1b0f5a0b48c452c3d2afd51f068d68563d743 | 027fab50-2478-4dd2-962f-bb525b36810d | Turkish targeting: data.country_code.toLowerCase() == ’tr' |
| 3281ffd83dccccd3aded58b14eb2196625b509bc49aa45c7b58c6bbfb495653e | cee6d18e-5adb-4fbd-b47b-989768473c66 | Australia targeting: data.country.toLowerCase() == ‘au’) drops lnk 64e9d8222c98fdc7f2f31428cae1d3172bf55882bed9aa9420f133dbe7fb64d0 |
| d76ec936e709f6e1e61827f0e8ca0cd5261202362207e9efcd9a87cdd8c386aa f162b9a38fe304e2fba800bb7c1207015f24bf6257f46caa6d587cfc4875ea97 |
b6f523d6-a9fb-41ae-9eb1-849d01249c41 46834616-9dd0-4544-b8ce-37e8e1d18065 |
Italy targeting: data.country_code.toLowerCase() == ‘it’ Ukraine targeting: data.country.toLowerCase() == ‘ua’ drops fake windows updater a9f84a4d517ea692dc036d9c5c5a577a14f050a6a1780c9974a8064efe33a9c9 install-kb-5021042.cmd 043e70796f7f36ca99ced36e473317f02f699b938148396dfd3515092c4d3bd3 windows-kb5021042.cab 0c50f6f2841093a6a27a3c60df8abfa0bdb87d01037840c3633918ae69b2e49f |
| a8d9850ac86e0498f6ba3abec5d4bb8366d7a20befffd9134f75332a93c79f7f | f75f0793-af82-43e0-af51-953944c45c9d | fetches docs_link.zip 1c5b7f0d4ea21c5e9413e7ff0f2cf364a560927446af7dac82b16e8e201be1a0 drops .lnk, .url, .website |
| cda936ecae566ab871e5c0303d8ff98796b1e3661885afd9d4690fc1e945640e | 66d5b9f9-a5eb-48e6-9476-9b6142b0c3ae | Includes decoy of https://i.ibb[.]co/vVSCr2Z/car-for-sale.jpg, keeping with long-time theme “diplomatic car for sale”. IMG-387470302099.jpg.exe c6a91cba00bf87cdb064c49adaac82255cbec6fdd48fd21f9b3b96abf019916b WindowsCodecs.dll 6b96b991e33240e5c2091d092079a440fa1bef9b5aecbf3039bf7c47223bdf96 zqtxmo.bat a06d74322a8761ec8e6f28d134f2a89c7ba611d920d080a3ccbfac7c3b61e2e7 related windows10.0-kb2911993-x64_6e4ef105-3c5a-48a4-957e-6dcb6833a94c.zip 0df548e0d1323e228a5608b1c1aff6d683f553ed6752460ac27d5874fa59d3e7 IMG-912566491.zip 836419b4a81302f60c8abd1a7503f42a1ed449f6635b88272a18eecfa164134e lehvtmpegkcczphm.bat 576b40065ab3d7718a5742fa7c739eebda046664528755726364af336fe2eace WindowsCodecs.dll dfed015bb3d47ce851c7cd6cef1b784ea5061e9811fec5416b8db5ea6c9566de WindowsCodecs.dll 2ea042ff11d0f972a2bd3610fcf0a767ff74f7e9f2729354889367554085100a |
Figure 5: Subsequent artifacts can be pivoted to, which gives quick detection wins
As a bonus for the first article in this series, we wanted to highlight how “decoy” content is an excellent indicator. More on this in part 2!
| .bat file | windows update decoy |
|---|---|
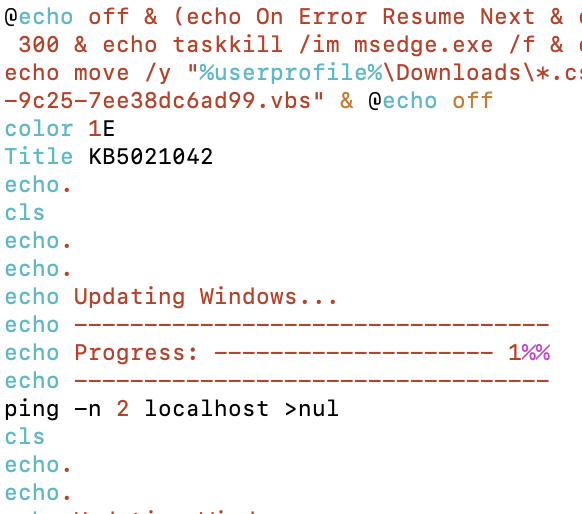
|
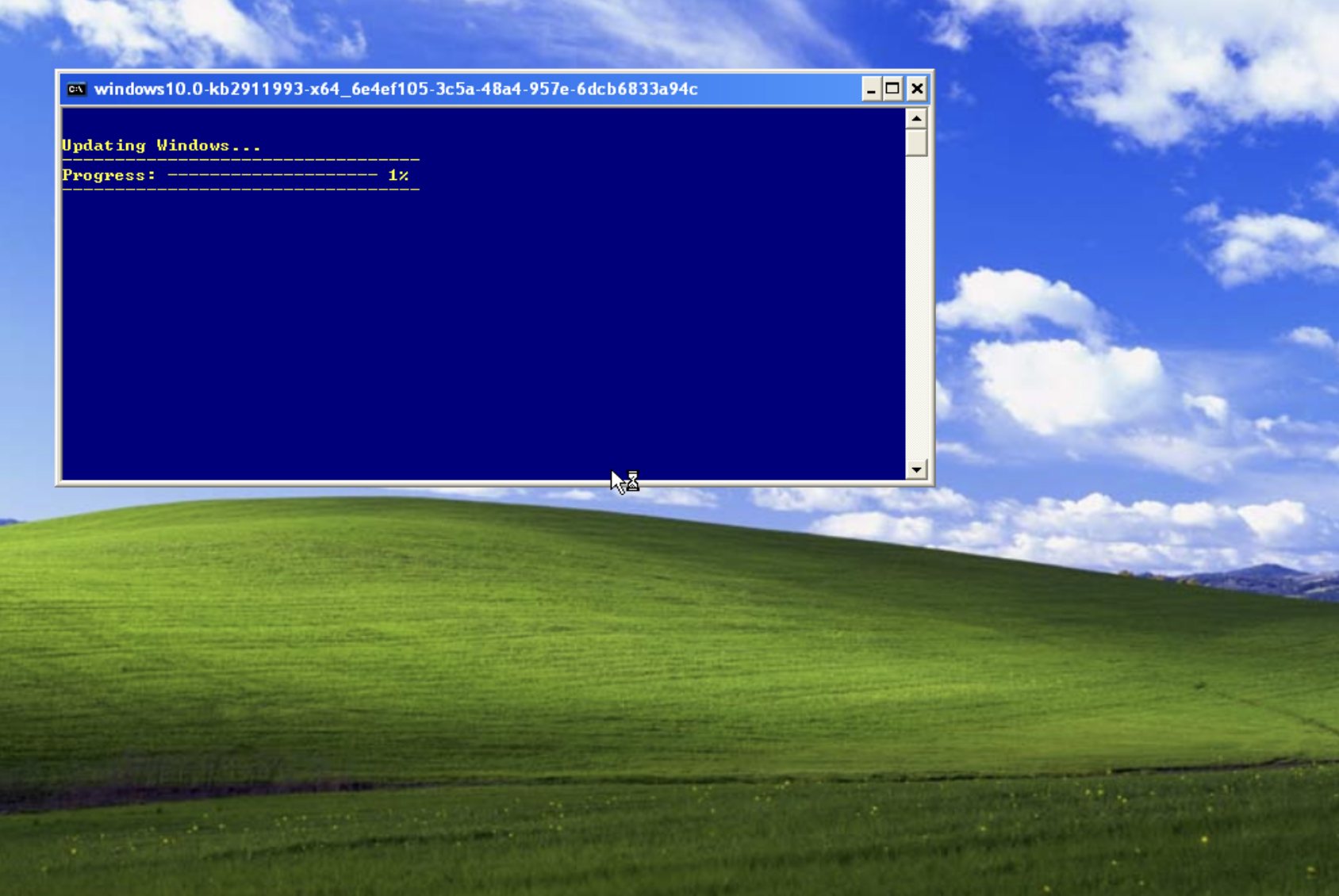
|
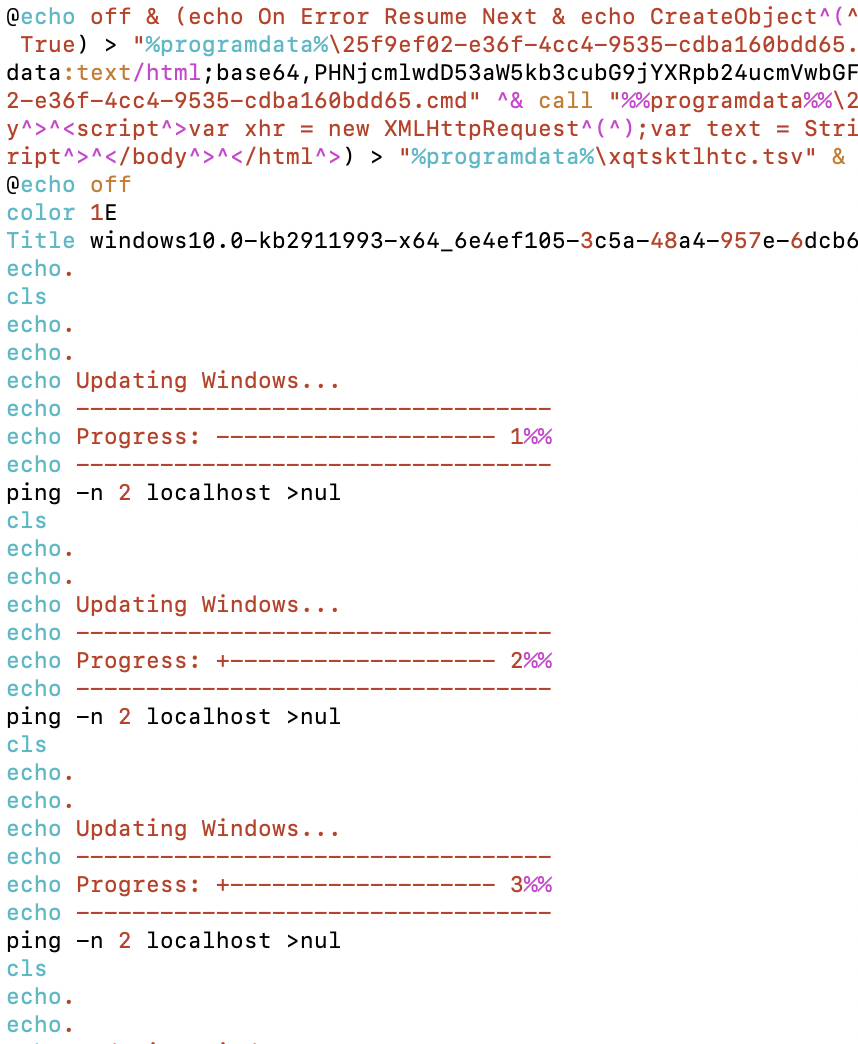
|
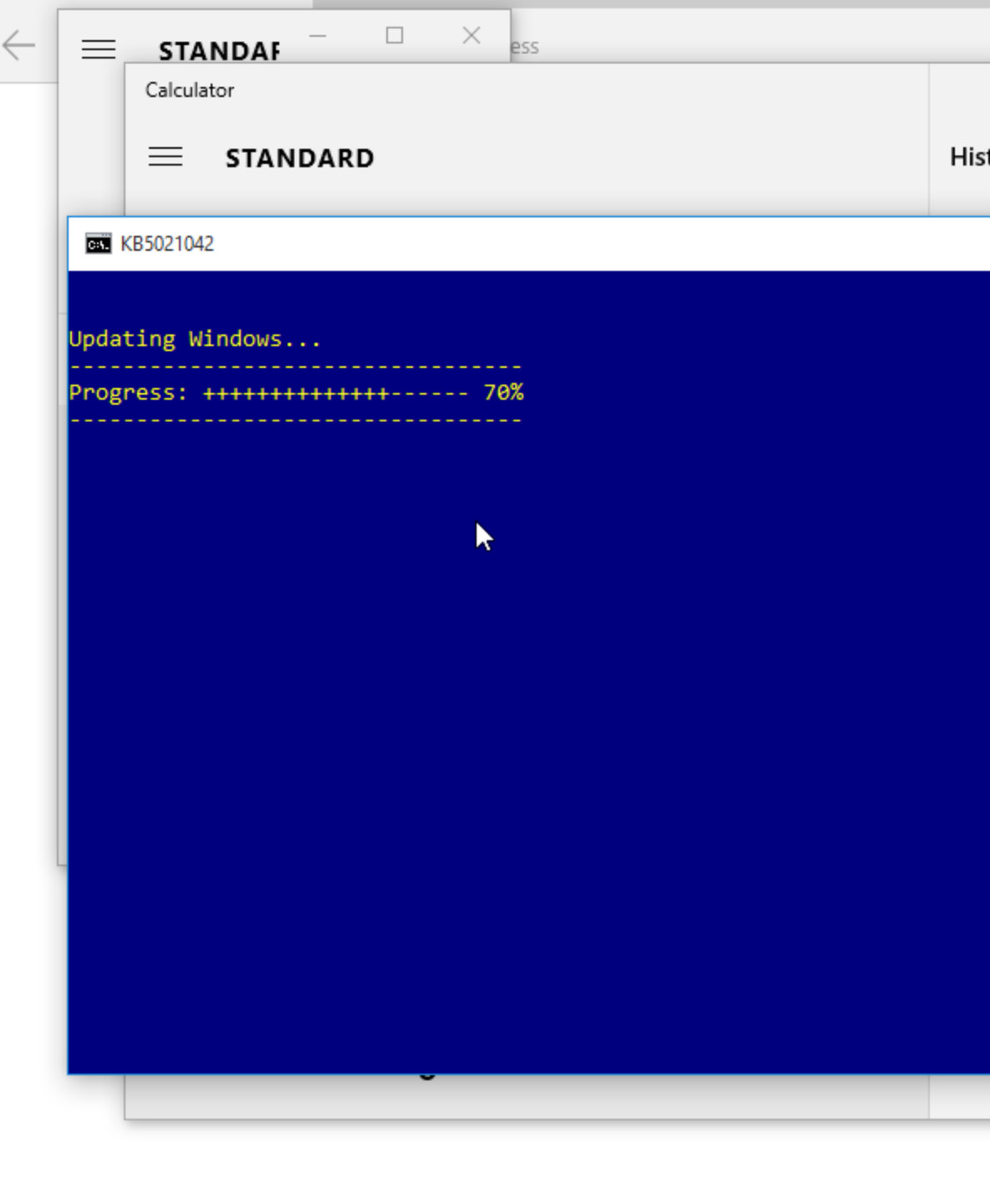
|
Figure 6: Decoy content – stick around for our next blog!
For an easier to parse list of indicators, please visit our GitHub page. Lastly, If you are a vendor, and wish to provide a statement of suspected attribution, please drop us a note, and we’ll add it for posterity.
| Vendor | Threat Actor name |
|---|---|
| Proofpoint | TA422 (section 2 above) |
Figure 7: Other validated vendor names for this actor
Acknowledgements
The authors would like to thank the reviewers, as well as peer vendors, for their comments and corrections. Specific thanks to Cybersixgill - Threat Intelligence Solutions | Cybersixgill for their assistance in reaching affected parties in Israel. Please get in touch at research@strikeready.com if you have corrections, or would like to collaborate on research.

