Recently an email was forwarded to Virustotal, appearing to show a ukr.net sender spoofing “Headquarters Police Department” (Головне управління поліції), targeting a government organization related to the Ukrainian economy.
Detection takeaways:
- The zip attachment was only 341 bytes, and the underlying attachment was even smaller at 134 bytes
- These very small sizes may bypass filters analysts or tools use to weed out junk files
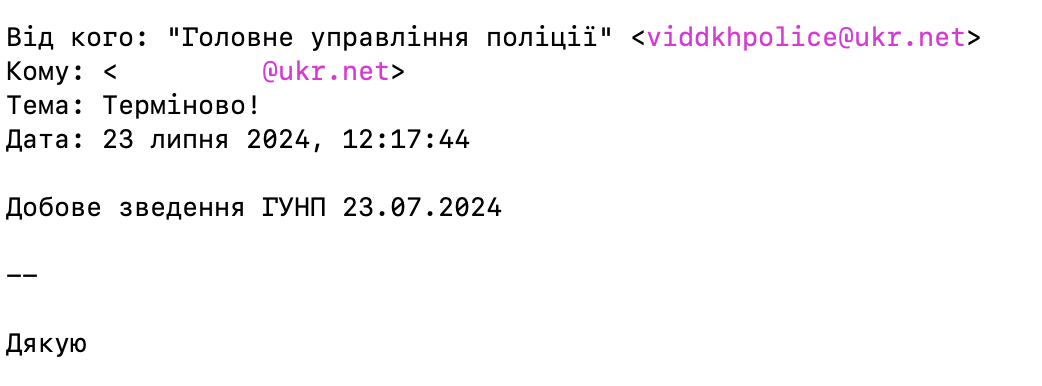
Figure 1: email spoofing a Ukrainian police org
| Attachment | sha256 | translated |
|---|---|---|
| терміново_23_07_2024.zip | c16926a74f8d30b4086057241edc46e88bb0cf675ff5b5ced93ea654ea2b4e26 | (urgently _23_07_2024.zip) |
| терміново_info_23_07_2024.html | 9e49db0eb920e130c0393a87c96434b9f0257025584cf546f623c1cb0b074333 | (urgently_info_23_07_2024.html) |
Figure 2: attachments to email
The initial HTML was very small, 134 bytes, and was simply a redirect to an external site.
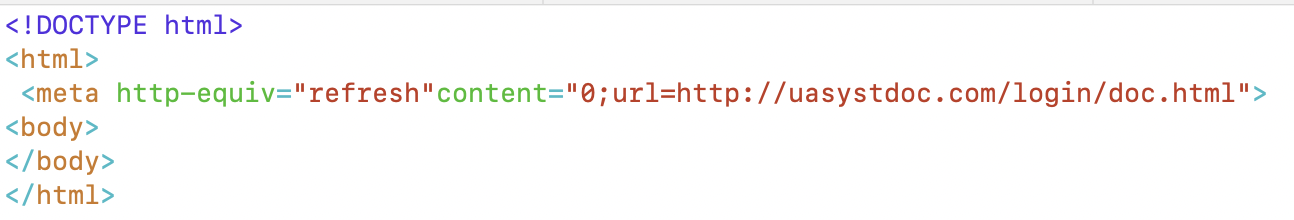
Figure 3: simple redirect, perhaps to prevent anti-spam detection
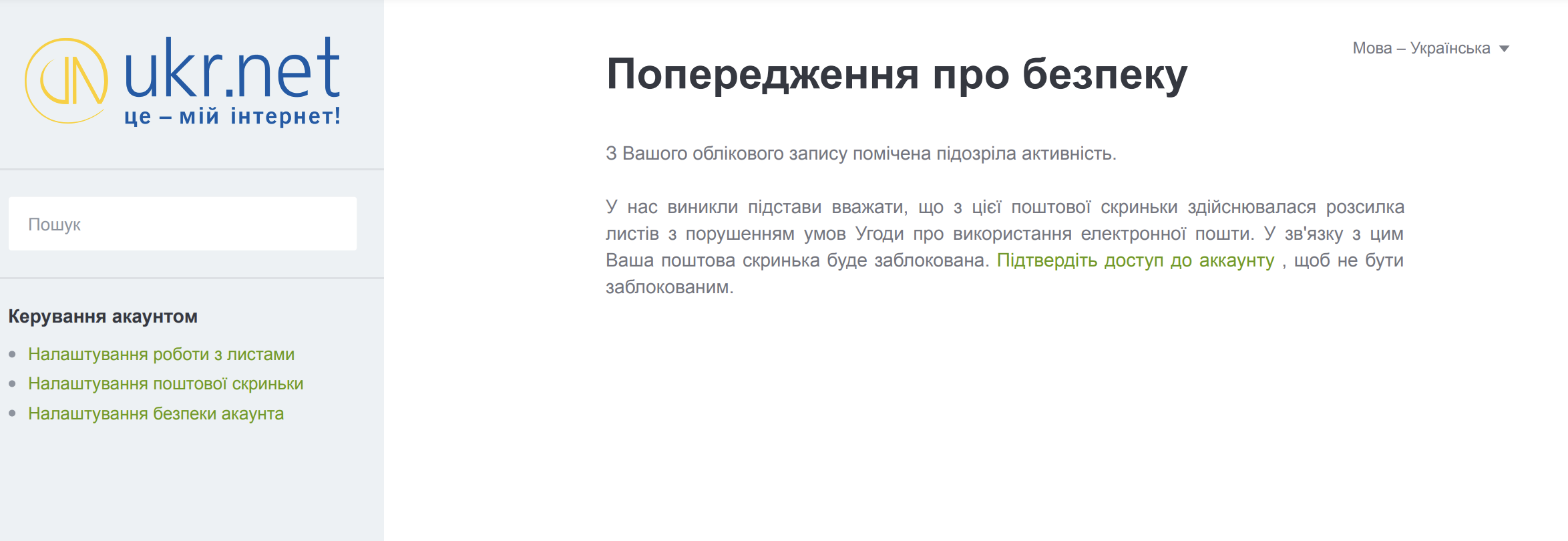
The page content is the below, and one can notice that it’s a phishing page for ukr.net, a Ukrainian webmail service. This service is a frequent target for Russia-nexus threat actors.
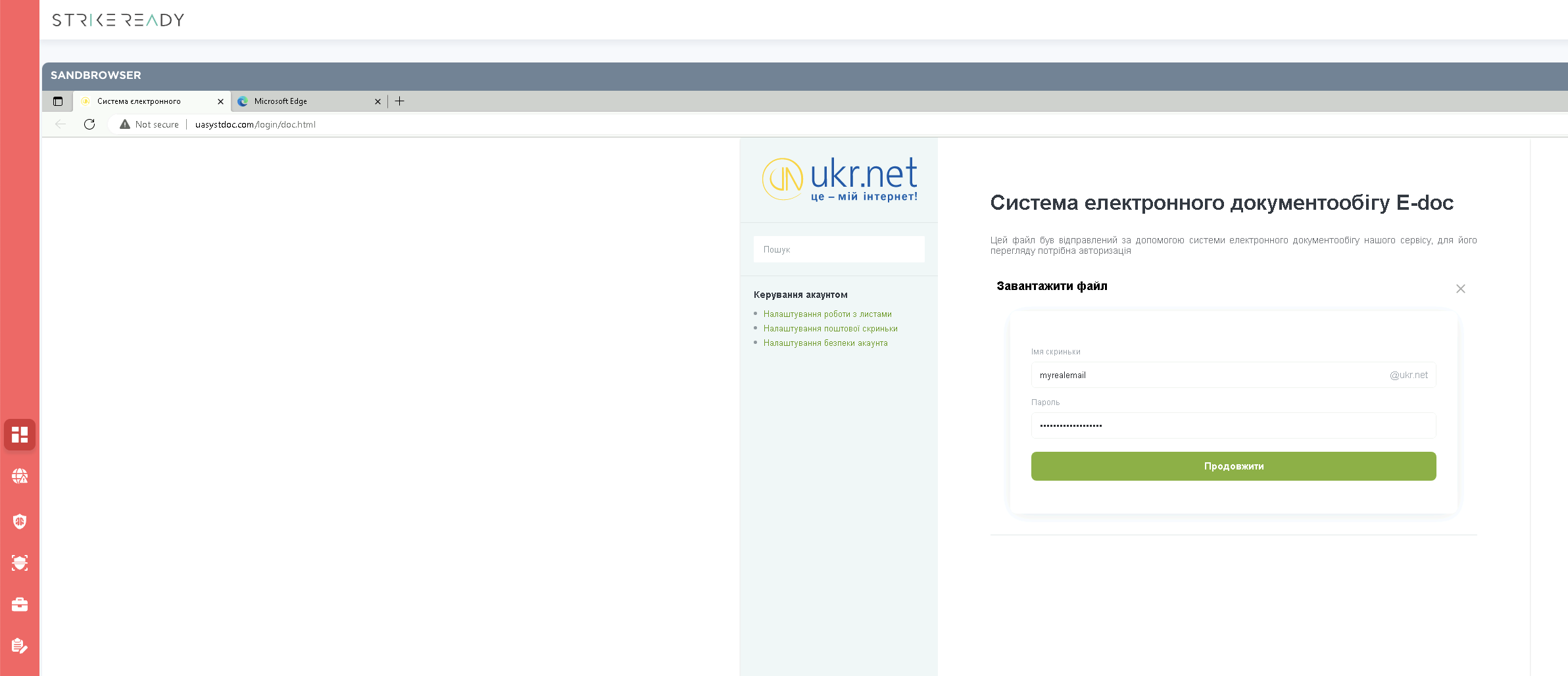
Figure 4: UKR credential phishing
The doc.html page contains a numerous amount of sig-able artifacts to find similar phishing pages. Signatures need not be written on malicious content to be effective. In the below example, the <head lang="uk"> is unusual. lang= is typically inside a <html> tag instead of <head>, but when you can combine this with other indicators, two weak signals can become a strong signature.
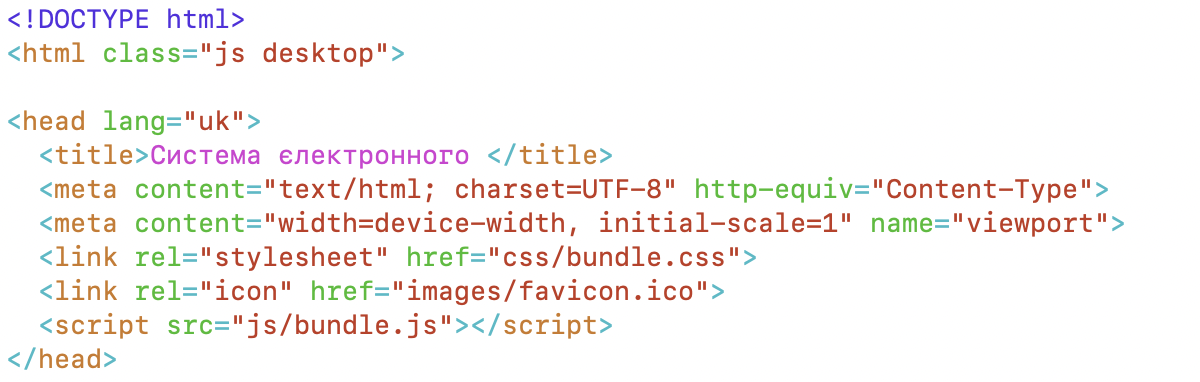
Figure 5: snippet of doc.html
| landing pages | sha256 |
|---|---|
| doc.html | efd54e566767de3e35597dae60d317b388460ffc2b3231bd4897b254863835cc |
| index.html | 5d93ee6f0f4e88d06f384a84ec4401100ec6b1d01062af23acebd3f314379be0 |
| file1.html | 5b694114129846328da15d79e2bc6a4b19f887e86ae8f0abc6d9572a8b88e431 |
Figure 6: associated landing pages
Examining the landing pages, we can notice the credentials will be POST’d to a PHP script and then redirected.
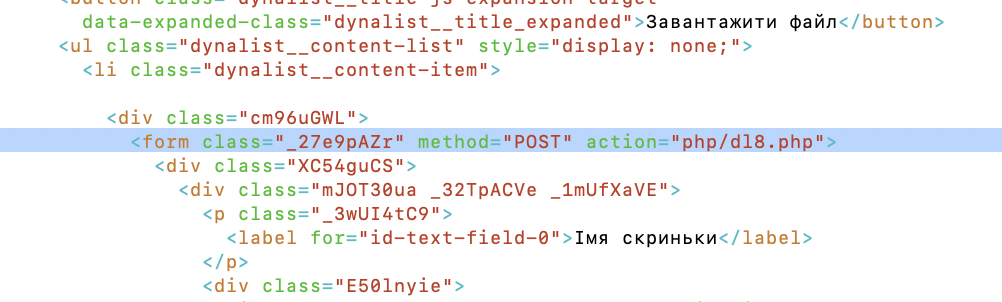
Figure 7: Analysts raise an eyebrow at “dl8”
After the credentials are sent, the PHP script redirects us to a decoy that might be interesting to a Ukrainian target. When analysts see “dl8.php”, they typically wonder what may live at “dl1.php”, “dl2.php”, etc.
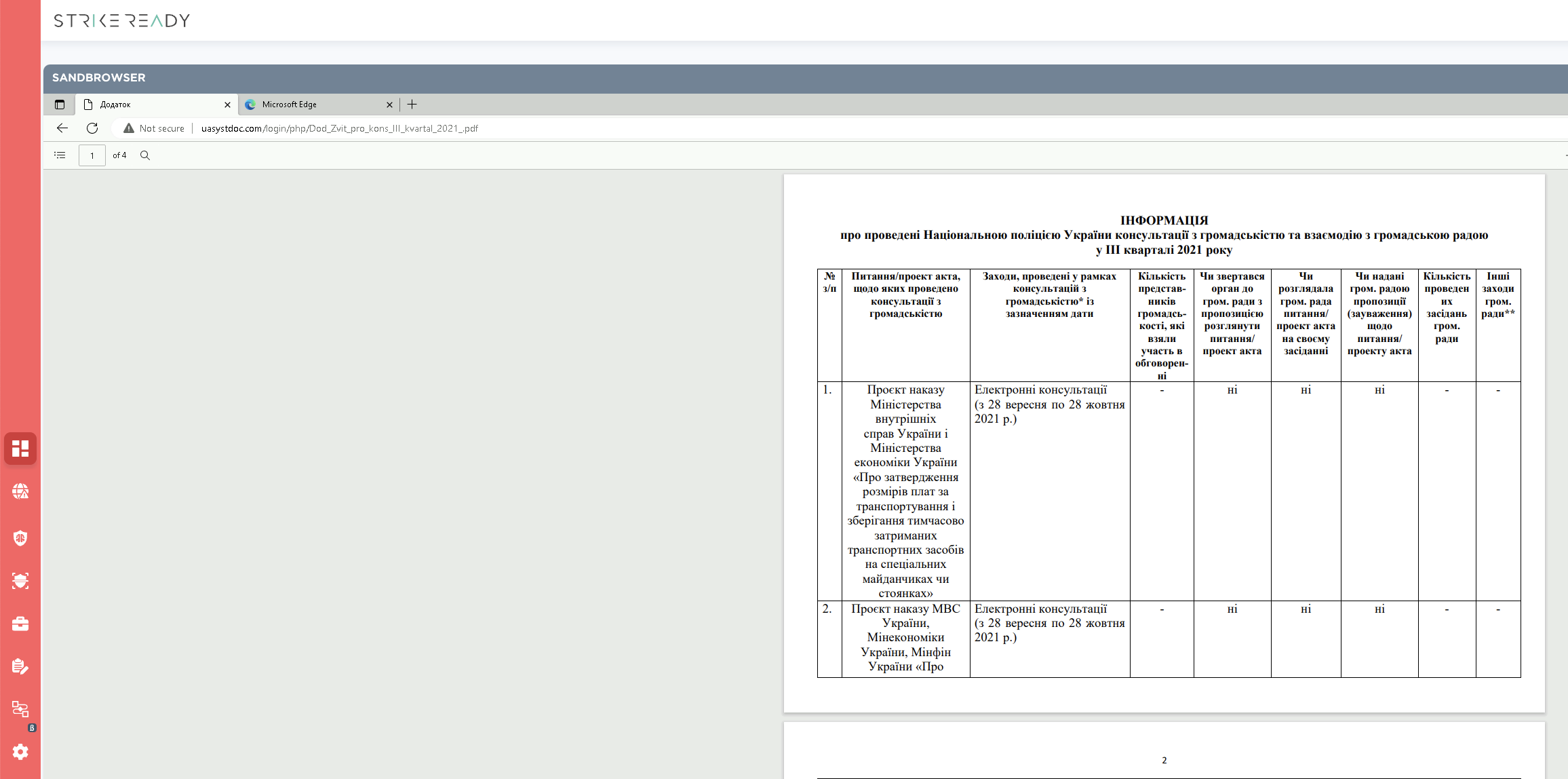
Figure 8: decoy content after credentials are entered
After looping through dl[0-9].php, we can harvest a number of other interesting decoy files as well as IOCs.
| dl.php | 82.221.139[.]200/login/php/1308_8711629.html |
| dl2.php | 82.221.139[.]200/login/php/zrazok.pdf |
| dl3.php | 82.221.139[.]200/login/php/organizations_kharkiv_2021_12_03-1.xlsx |
| dl4.php | 82.221.139[.]200/login/php/47.pdf |
| dl5.php | 82.221.139[.]200/login/php/tsu-sbu-vid-13042023-131-site.doc |
| dl6.php | ukainua[.]com/login/php/d534990-20240427.pdf |
| dl7.php | ukainua[.]com/login/php/Dod_Zvit_pro_kons_III_kvartal_2021_.pdf |
| dl8.php | uasystdoc[.]com/login/php/Dod_Zvit_pro_kons_III_kvartal_2021_.pdf |
Figure 9: credential gathering and decoy redirecting scripts
A sampling of the decoy content is show below.
| zrazok.pdf | 47.pdf | d534990-20240427.pdf |
|---|---|---|
 |  |  |
Figure 10: three of the decoy files from the table above, showing Ukrainian themes
A quick pivot to passivedns through our community account at silentpush shows many likely related domains, shared in our github.
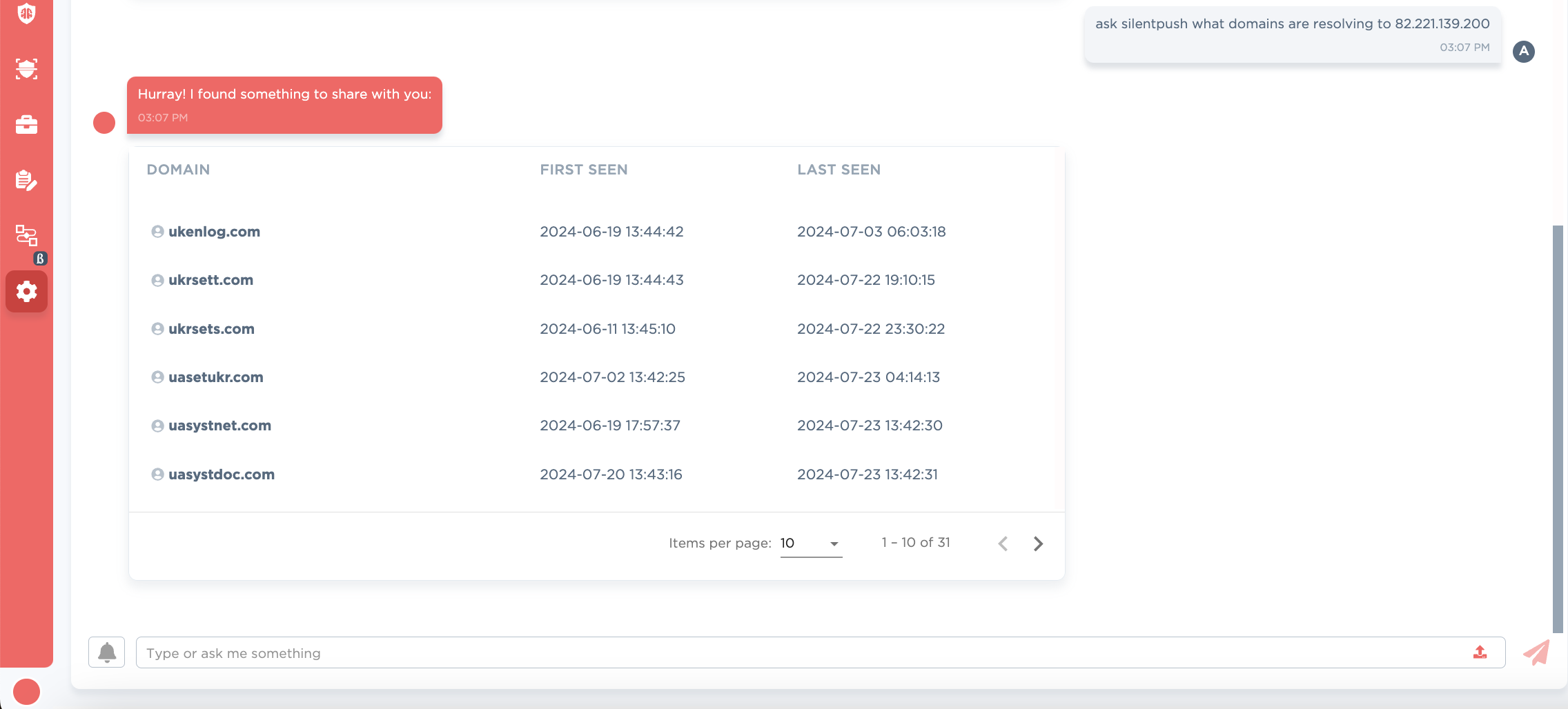
Figure 11: passive dns for 82.221.139[.]200
Lastly, pivots on the layout of the phishing page, combined with negating legitimate infrastructure, will lead to similar phishing campaign.
| Phish | IOCs |
|---|---|
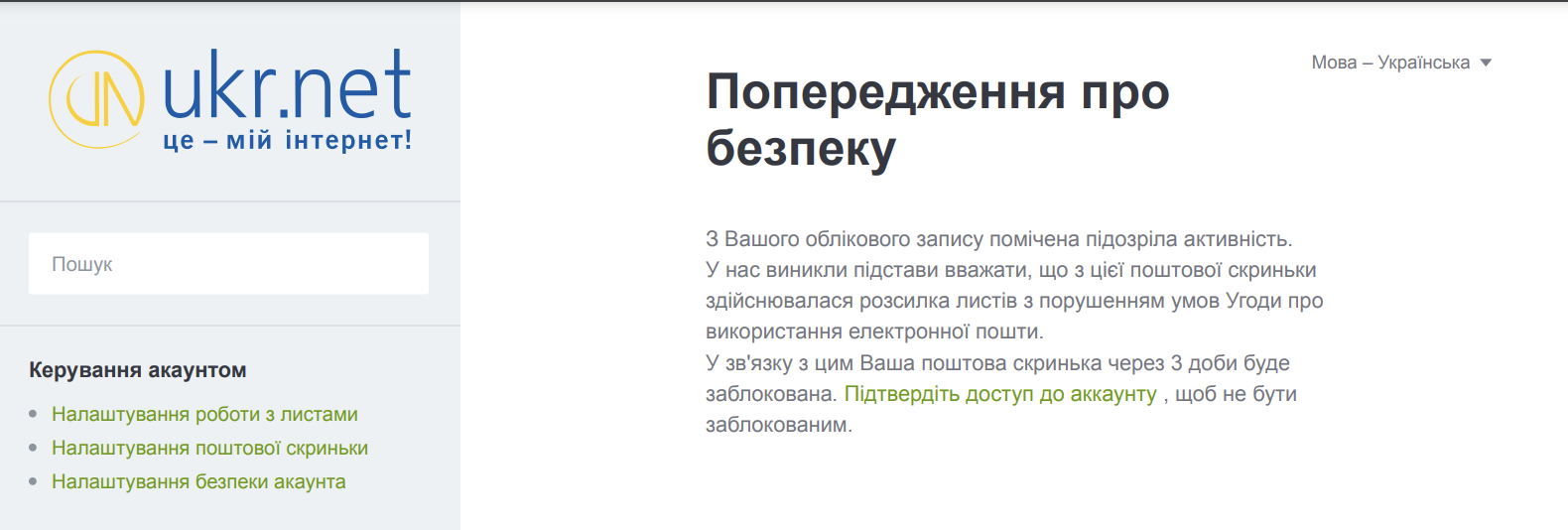 Figure 12: UKR.NET.pdf | changepassword-ukr[.]net/desktop/security/login/ 38963b61113b7b88e3fce30539e63b4745f8d91f8e2577b6597a09648b105733 |
 | accounts.ukr-reset[.]email/login/ 2f1f4b077b6fc40d8f0c995e80657448478a08acdf0e33ee2b73602bda62270c |
 Figure 13: Попередження.pdf | accounts.ukr-mails[.]net/login 853f21ba9a8a362a9bafc98204eb70b8c23ba845359e694984711ec1485d0c2f |
 | accounts.kv-ukr[.]net/login/ e159886a173f021b345ad152ad84beed3ac39b6a7455805c255f38d7b4c9434c |
| Vendor | Threat Actor name |
|---|---|
| Google Cloud Security (neé Mandiant) | UNC3707 |
| You? | Get in touch for blog pre-releases! |
Figure 14: Other validated vendor names for this actor
Our github provides a download to the raw samples mentioned in the blog, as well as the indicators.
Acknowledgements
The authors would like to thank the reviewers, as well as peer vendors, for their comments and corrections. Please get in touch at research@strikeready.com if you have corrections, or would like to collaborate on research.





